Password Management Utilities For Mac
There's sort of a fourth method, implemented by 1Password, to encourage app authors to and searches for the appropriate login. But that's all it does. It can't switch back to the app or auto-fill fields, so the user has to copy the credentials to the clipboard, manually go through the home screen back to the app and paste them. Nobody gets it right.
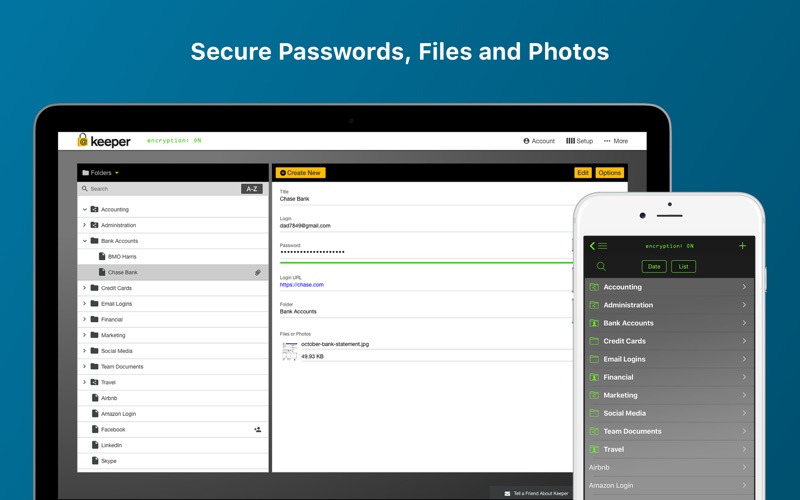
Password managers are great because they store all your passwords, generate strong ones for you, and in general, the only password you have to remember is the one to open your password manager. Now the best password managers give you the option to sync or keep them local only, change web passwords with a click, log in to sites for you, and more.
However, one disadvantage of this design is that the kinds of techniques used for multi-step authentication are entirely inapplicable to 1Password. Those techniques are designed to add requirements to an *authentication* process, but unlocking your 1Password data is **not an authentication process at all**. How to disable popup blocker on chrome for mac free. Because there is no 1Password “server”, there are no (additional) steps we can insist on as part of a (non-existent) login process.
You can also choose to verify with another device if you choose. How to Manually View Credit Card Numbers with iCloud Keychain • Launch the Settings app on your iPhone or iPad. • Tap on Safari. • Tap on Passwords & AutoFill under the General section. • Tap on either Saved Passwords or Saved Credit Cards. I find it particularly helpful that I can now access Keychain info on either my iPhone or my iPad. Before this became an option I always had to wait until I was at my Mac to transact business.
When you put all of your passwords into one repository, you had better be really, really careful to protect that repository. Yes, your master password should be as strong as possible, but you really need two-factor authentication to foil any possible hack attack. Two-factor authentication could be biometric, requiring a fingerprint, facial recognition, or even voice recognition. Some password managers rely on Google Authenticator or apps that emulate Google Authenticator; others use an authentication code texted to your smartphone. Allowing access only from registered, trusted devices is yet another form of two-factor authentication. Speaking of smartphones, many of us are just as likely to log into a secure site from a mobile device as from a desktop computer.
Do this, log out of your account and then back in; when the Mac needs to use one of the passwords stored in the login keychain, you’ll be prompted to enter it. As long as you’re logged in, you shouldn’t be troubled for that password again. Auto-lock the keychain By default, once you’ve logged in, your keychain will be unlocked, which isn’t terribly secure if others can access your Mac when you’re not around. You can add a level of security that auto-locks your keychain. To do that, launch Keychain Access, select your login keychain, and choose Edit > Change Settings for Keychain “login”. The sheet that appears shows two options: 'Lock After X Minutes of Inactivity' and 'Lock When Sleeping'.
I won’t repeat why we haven’t moved on this (yet), but it is something that is under consideration. Basically we need to find a way to do this that won’t lead to unacceptable rates of people losing access to their data. Unlike authentication where tokens can be reset server side, if someone loses or damages this second factor there is absolutely no way to ever unlock the data again. I also found it odd when you said, “But for its price, it better focus heavily on security in addition to looking great on Macs, right?” Just because 1Password is beautiful don’t imagine that it doesn’t have brains. In evaluating the security of password managers, it is important to look at the actual design of the system carefully.